Boost your infrastructure. Start using our services today.
We've a variety of services aimed at bettering your infrastructure, and preventing cyber attacks, by adopting a pro-active security posture in your company.
Quick Navigation
Strategic cloud architecture and security-first engineering across AWS, Azure & GCP — resilient, compliant, and cost-efficient cloud platforms built to scale.
End-to-end multi-cloud security: from hardened configurations and compliance audits to fully operationalized cloud-native security tooling.
Seamless cloud migrations with performance, security, and cost-efficiency built in—maximize ROI without disruption.
Proactive threat modeling that uncovers risks before attackers do—integrated into your cloud, apps, and development lifecycle.
Secure, automated pipelines and infrastructure—built to deliver faster, safer, and more reliable software at scale.
Enterprise-grade Kubernetes: secure, observable, and resilient clusters that power microservices at scale.
Use professional advice to better your cloud environment
Cloud Consulting
We design cloud architectures that align technology with business outcomes. Whether you're on AWS, Azure or Google Cloud, we create cloud-native architectures, landing zones and platform roadmaps that balance performance, reliability and cost. Our governance models and operational patterns make environments easier to operate and audit—so your teams move faster while your platform remains resilient and compliant.
Security is not an add-on — it's baked into every product and decision. From day one we apply threat-aware design, secure defaults and the principle of least privilege, combined with automated security testing and developer-friendly guardrails. The result: significantly lower risk exposure without slowing feature delivery, because security and speed are designed to work together.
We deliver infrastructure as code you can trust. Using Terraform and SDK-based tooling, policy-as-code, automated IaC tests and secure state management, we produce repeatable, auditable deployments that reduce human error and accelerate recovery. This approach makes upgrades, scaling and compliance checks predictable — and gives you a clear audit trail for security and regulatory needs.
Work with us to turn cloud complexity into a strategic advantage. Whether you need a cloud strategy, a secure platform foundation, or production-grade IaC, we provide pragmatic, measurable plans that align to your risk appetite and budget. Ready to secure your cloud journey? Contact us for a tailored architecture review and roadmap.




Secure your infrastructure
Cloud Security
Cloud platforms are powerful, but without the right safeguards they can expose organizations to costly risks. We help you secure your AWS, Azure, and Google Cloud environments with a holistic approach—covering identity, encryption, logging, network segmentation, and service configuration hardening. By aligning controls across providers, we make sure your security posture is consistent and reliable, no matter where you run your workloads.
Compliance is no longer optional—it's a requirement for winning customer trust and meeting regulatory obligations. Our cloud security audits and assessments give you a clear picture of your strengths and gaps. We prepare audit-ready evidence, map controls to industry standards such as ISO, SOC 2, GDPR, and PCI, and build a prioritized roadmap so you can pass assessments with confidence and efficiency.
Technology alone doesn't solve security challenges—it needs to be implemented and tuned properly. We deploy and operationalize both cloud-native and third-party security solutions, from AWS Security Hub, Microsoft Defender, and Google Security Command Center to CSPM and CIEM platforms. With us, you get properly configured tools, meaningful alerts, and clear response playbooks—so your teams can act quickly without drowning in noise.
Partner with us to transform cloud security from a compliance checkbox into a competitive advantage. With proactive controls, transparent reporting, and automated defenses, you can scale in the cloud while knowing your data, users, and workloads are secure.
Better Infrastructure
Cloud Migration & Cost Optimization
Moving to the cloud doesn't have to mean downtime, spiraling costs, or endless complexity. We plan and execute migrations that minimize disruption and risk, ensuring your workloads arrive in the cloud secure, stable, and ready to scale. From rehosting to full re-architecture, we match the right approach to your business priorities.
But migration is just the beginning. Once your systems are running in AWS, Azure, or Google Cloud, we help you get the most out of your investment. Through rightsizing, reserved instances, savings plans, and architecture refinements, we reduce unnecessary spend while maintaining performance and compliance. You'll gain predictable costs, stronger ROI, and an environment tuned for both efficiency and growth.
Whether you're modernizing legacy applications or consolidating multi-cloud environments, we make sure your cloud foundation delivers long-term value—not just a one-off migration.
Get insight in threats your business faces
Threat Modeling
Threats evolve quickly, but most organizations don't discover them until it's too late. Our threat modeling services identify and prioritize risks across your applications, infrastructure, and supply chain—before attackers can exploit them. We deliver actionable mitigation plans that balance security with delivery priorities, ensuring security fits naturally into your engineering workflow.
Cloud platforms introduce unique risks that require cloud-native thinking. From misconfigured IAM roles and abused service accounts to metadata API exposures and lateral movement inside VPCs, we help you map and mitigate provider-specific attack vectors. Our recommendations are pragmatic, tested against real-world scenarios, and tailored to AWS, Azure, or Google Cloud environments.
Threat modeling isn't just a one-time activity—it should evolve with your product. That's why we embed security analysis into design reviews, agile sprints, and pull requests. Risks are continuously tracked, prioritized, and remediated as part of your normal development process, not as a last-minute compliance checkbox.
With us, threat modeling becomes a strategic tool, not an overhead. You'll gain clear visibility into your attack surface, reduce costly rework, and build customer trust by proving that security is integral to how your products are built.
Deploy faster & More Secure
DevSecOps / DevOps
Secure, automated pipelines and infrastructure—built to deliver faster, safer, and more reliable software at scale.

Modern delivery requires both speed and security. With our DevSecOps expertise, we embed security into every stage of your development and operations process—so you can release faster without introducing risk.
- CI/CD & secure pipelines — Automated pipelines with secrets management, artifact signing, dependency scanning, and policy gates that prevent insecure code from reaching production.
- Terraform & IaC security automation — Shift-left infrastructure scanning, policy-as-code validation, and drift detection to ensure every change is secure before deployment.
- Automated security — Build-time and runtime scanning (SCA, SAST, DAST) with automated remediation workflows that cut manual effort and reduce response times.
These practices transform DevOps from a delivery function into a secure, resilient engine for your business. Security becomes invisible to developers yet reliable for operations—enabling teams to innovate confidently.
From pipelines to culture
DevSecOps isn't just tooling—it's a way of working. By embedding guardrails, automation, and continuous feedback into your lifecycle, we help your teams move faster while knowing every release is secured by design.
Deploy faster
Kubernetes
Kubernetes is the backbone of modern cloud-native applications—but managing it securely and efficiently requires deep expertise. We help you design, deploy, and operate Kubernetes environments that balance agility with governance, enabling teams to deliver faster without compromising reliability or compliance.
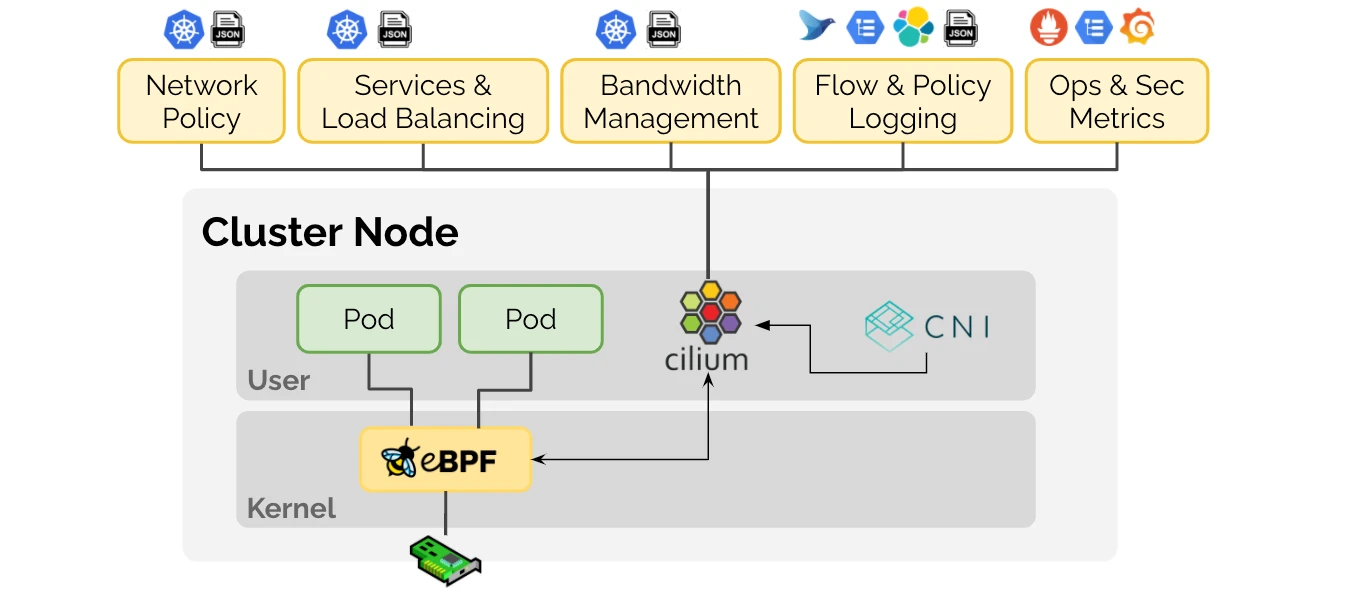
Networking inside Kubernetes is complex. With service meshes, we enable secure, observable communication between microservices, complete with mTLS, traffic management, and granular monitoring. Our expertise with eBPF-based tooling and Cilium takes this further—delivering high-performance networking, fine-grained policies, and deep visibility into traffic flows at the kernel level. This ensures your clusters scale smoothly while maintaining control.
Security and compliance are central to our Kubernetes approach. We harden clusters against threats, secure the software supply chain, and enforce RBAC, Pod Security Standards, and network policies. Whether you're preparing for an audit or operating in a regulated industry, we provide the controls and evidence you need to meet compliance confidently.
With our Kubernetes services, you don't just get clusters that work—you get platforms that are resilient, secure, and tailored to your business needs.